How to Check the Permissions of Your Microsoft Graph Application Via JWT

Check the Permissions of Your Microsoft Graph Application using Access Token (JWT)
To ensure that your Microsoft Graph application is functioning properly, it is important to check its permissions (go here for a full list of graph permissions). This will help you make sure that the app has the necessary access to perform the tasks it was designed for.
This article explores how you can automatically validate your app's roles without manually logging into Entra/Azure to check. More specifically:
- How to automatically/programmatically check the permissions assigned to your Microsoft Graph Application?
- How do you get the roles of your Graph Application without accessing Entra or Azure?
- How to retrieve Entra Built-In Roles assigned to the Graph Application?
How to Check Graph Permissions Using Powershell?
You can check what permissions/scopes your application has by using Powershell via the Get-MgContext cmdlet.
The necessary steps are as follows:
- Install PowerShell 5.1 or later
- Install Microsoft Graph Powershell Module
- Connect to Graph using your client Id, secret and tenant Id (assuming Client/Secret credentials)
$ClientSecretCredential = Get-Credential -Credential "<enter-your-app-id>"
# Enter client_secret in the password prompt.
Connect-MgGraph -TenantId "<enter-your-tenant-id>" -ClientSecretCredential $ClientSecretCredential- Run the
Get-MgContextcommand and look at the “scopes” returned:
PS /Users/ckarawani> Get-MgContext
ClientId : 8820d97a-210c-4b91-8d7c-fakeclientid
TenantId : 0d64725c-6eea-4ee0-a981-faketenantid
Scopes : {User.ReadWrite.All, GroupMember.ReadWrite.All} ✅
AuthType : AppOnly
TokenCredentialType : ClientSecret
CertificateThumbprint :
CertificateSubjectName :
Account :
AppName : easy365.io example app
ContextScope : Process
Certificate :
PSHostVersion : 7.3.6
ManagedIdentityId :
ClientSecret : System.Security.SecureString
Environment : GlobalHow to Get Microsoft Graph Roles by Evaluating the Access Token (JWT)?
When using Graph via REST/HTTPS, you can inspect the JWT (JSON Web Token) used for authentication to verify the permissions/scopes your application has assigned.
For example, when making a call to authenticate
curl --location 'https://login.microsoftonline.com/dev-stack8.com/oauth2/v2.0/token' \
--form 'client_id="8820d97a-210c-4b91-8d7c-fake-client-id"' \
--form 'client_secret="XXXXXXXXXXXX"' \
--form 'scope="https://graph.microsoft.com/.default"' \
--form 'grant_type="client_credentials"'You’ll get back a JSON response containing a bearer token under the access_token attribute
{"token_type":"Bearer",
"expires_in":"3599",
"ext_expires_in":"3599",
"expires_on":"1703130558",
"not_before":"1703126658",
"resource":"https://graph.microsoft.com",
"access_token":"eyJ0eXAiOsD0pcaceCif67Q..."} // ❗️ Grab this token!!You can inspect this bearer token by navigating to https://jwt.io and pasting it into the page with the default RS 256 algorithm:

You can decode the JWT and determine the roles assigned to your Microsoft Graph app in any programming language:
- How to decode JWT in Java
https://www.baeldung.com/java-jwt-token-decode - How to decode JWT in Python
https://medium.com/geekculture/how-to-encode-and-decode-jwt-token-using-python-f9c33de576c5 - How to decode JWT in Powershell
https://www.michev.info/blog/post/2140/decode-jwt-access-and-id-tokens-via-powershell - How to decode JWT in Javascript
https://github.com/auth0/jwt-decode
How to get Built-in Roles Assigned to Graph Applications?
There are certain scenarios where an Entra Built-in Role will need to be assigned to your application. These are different than the graph roles.
A common use case — you need a Teams Administrator role to perform many use cases via the Microsoft Teams PowerShell module with app-based authentication.
How to get Built-In Roles Assigned to Graph API using Powershell (not possible 😢)?
Unfortunately, the Powershell Command for Graph Get-MgContext does not return such information. An issue/request is currently open here. Bummer…
How to get Built-In Entra Roles Assigned to Graph Application using Access Token (JWT)?
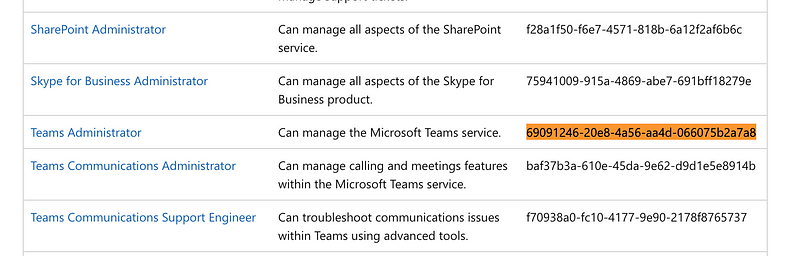
Fortunately, the access token contains a property called wids that provides this information (via Template ID)

For example, the ID 69091246–20e8–4a56-aa4d-066075b2a7a8 is that of the Teams Administrator Role.
You can consult the full list of Built-In Roles and their associated Template IDs via the Microsoft Entra Build-In Roles Reference.
By utilizing the recipes that I have shared, you can now effortlessly retrieve and validate the assigned roles of a Graph Application in a fully automated and programmatic manner.
Say goodbye to reaching out to your Azure admins or manually accessing Entra to check your app roles! Happy coding! 🤓